What is the term for the unauthorized modification of data within a database by exploiting vulnerabilities in an application’s software?
- A. Ransomware
- B. SQL injection
- C. Spoofing
- D. Phishing
What was the primary advancement of the EDVAC over the ENIAC?
- A. Use of Vacuum tubes
- B. Smaller size
- C. Stored-Program architecture
- D. Faster computation speeds
What is the relationship between a ‘record’ and a ‘file’?
- A. A record contains multiple files
- B. A file is a type of record
- C. o A record and a file are the same
- D. A file contains multiple records
Which stage of the SDLC involves evaluating the system to ensure it meets user needs and making necessary adjustments?
- A. Review
- B. Implementation
- C. Analysis
- D. Design
Which key on a keyboard is used to access special functions like volume control or brightness?
- A. Alphabetic key
- B. Numeric key
- C. Function key
- D. Cursor key
Which of the following best describes the SDLC?
- A. A programming language for system development
- B. A framework for developing information system
- C. A methodoloy for software debugging
- D. A hardware configuration protocol
Which of the following best describes software?
- A. Elements used for data transmission
- B. Logical sequences of coded instructions
- C. Systems that control data flow
- D. Tangible components of a computer
Which application package is used for developing websites?
- A. Microsoft PowerPoint
- B. Microsoft Excel
- C. Figma
- D. Adobe Dreamwaver
Which access method is least efficient for data retrieval?
- A. Direct access
- B. Sequential access
- C. Indexed access
- D. Random Access
What does the ‘Thesaurus’ feature in word processing packages help users with?
- A. Find synonyms and antonyms of words
- B. Check document statistics
- C. Insert citations
- D. Create a table of contents
Which type of computer functions as a central repository, providing hardware, software, and other resources to multiple clients connected over a network?
- A. Workstation
- B. Mainframe
- C. Supercomputer
- D. Server
a – A principal asked the secretary to typeset a document containing some confidential information in Microsoft Word. The principal wants the document to be typed in such a way that when it is opened, the confidential information will be hidden from other users.
Highlight the steps the secretary would take to hide the confidential information in the document.
b – A principal asked the secretary to typeset a document containing some confidential information in Microsoft Word. The principal wants the document to be typed in such a way that when it is opened, the confidential information will be hidden from other users.
Outline the steps the principal would take to display the hidden text in 3(a) for viewing.
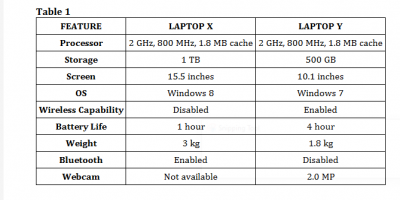
a – Table 1 shows the specification of two laptop computers. Use the table to answer questions 2(a) and 2c .
A journalist makes long trips by train as part of official assignments. The journalist also needs to make live communication with editors.
Which of the two laptop computers is more suitable for this journalist?
b – A journalist makes long trips by train as part of official assignments. The journalist also needs to make live communication with editors.
State three features of the chosen laptop in 2(a) that makes it better.
c – A journalist makes long trips by train as part of official assignments. The journalist also needs to make live communication with editors.
Give one reason for choosing each of the features stated in 2(b)
(i) The home network of a family has internet access. A server configured to control user access to the network.
State two problems that will likely happen if the children in the family have uncontrolled access to the internet
(ii) The home network of a family has internet access. A server configured to control user access to the network.
Suggest how the problems in 1(a)(i) can be prevented.
1(b) The home network of a family has internet access.
A server configured to control user access to the network.
Give one reason for the user control access
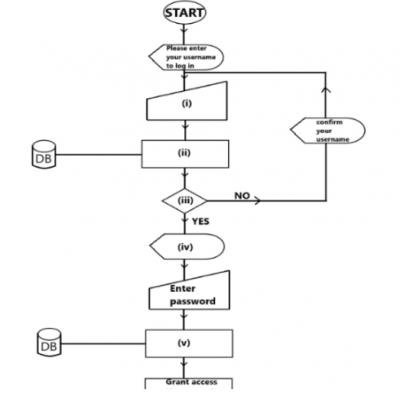
c(i) To have access to the network, each user logs in with a username and password. The flowchart in Figure 1 illustrates the authentication process required to log in. Use the information below to complete the flowchart by placing the letters A to E in the appropriate flowchart symbol numbered (i) to (v) :
A – “Please, enter password to log in”
B – Is the username found?
C – Search the username in the database.
D – Check the password.
E – Enter the username.
(i) ___________________________________________
c(ii) A – “Please, enter password to log in”
B – Is the username found?
C – Search the username in the database.
D – Check the password.
E – Enter the username.
(ii) ___________________________________________
c(iii) A – “Please, enter password to log in”
B – Is the username found?
C – Search the username in the database.
D – Check the password.
E – Enter the username.
(iii)___________________________________________
c(iv) A – “Please, enter password to log in”
B – Is the username found?
C – Search the username in the database.
D – Check the password.
E – Enter the username.
(iv) ___________________________________________
c(v) A – “Please, enter password to log in”
B – Is the username found?
C – Search the username in the database.
D – Check the password.
E – Enter the username.
(v) ___________________________________________
The process of making copies of files which can be used to restore the original copy in the event of data loss is called file
- A. restoration.
- B. retrieval.
- C. organization
- D. backup
Stored instructions and data in digital computer consist of
- A. bits.
- B. numerals.
- C. alphabets
- D. characters.
A program that converts source code instructions in high-level programming language to object codes line by line is known as
- A. interpreter.
- B. compiler.
- C. editor
- D. assembler.
Datatypes in QBASIC programming language include the following except
- A. double
- B. short
- C. float.
- D. long.
The database model that uses tables with columns and rows is called
- A. hierarchical database.
- B. relational database.
- C. network database.
- D. linear database.
Which of the following actions is not an animation in Microsoft PowerPoint?
- A. Entrance
- B. Emphasis
- C. Motion paths
- D. Dancing
Viruses, worms and Trojan horses are regarded as
- A. system software.
- B. malicious software.
- C. application software.
- D. utility software.


