As a database administrator for a company, create a table named tbl-Employee in a database application package containing the fields:
“Employee Name”, “Department”, “Assumption Date”, Address and “Designation”.
(a) Enter the data as shown in the table tbl-Employee
tbl-Employee
|
Employee Name |
Department | Assumption Date | Address | Designation |
|
Kate Willikie |
General Office | 03/08/18 | 3 Lagos Crescent | Secretary |
|
James Elliot |
Security | 27/11/10 | 2 Cocoa House Villa. | CSO |
|
Paul Akinson |
Admin | 03/11/12 | 12 Millo Avenue |
HRM |
|
Abdul Kaduna |
Registry | 05/06/16 | 2 Park Lane Rd |
Clerk |
|
David Madu |
Management | 22/03/94 | 34 Lakeside |
MD |
(b)Sort the data using the Assumption date from oldest to newest.
(c) Create a report in tabular, landscape using the tbl-Employee table.
(d) Insert your full name and index number as a label on the report.
(e) Save the report as rpt-Employee.
(f) Print your work and submit to the supervisor.
Use a spreadsheet application to do the following. (a) In cell A1, type “My One Week Expenses On Five items”.
(b) In row 2, type column-by-column the following: “ITEM”, 1ST DAY, “2ND DAY, “3RD DAY”, *4TH DAY, “5THDAY”, “6TH DAY” and “7TH DAY”.
(c) In column A, starting from A3 to A7, List the items you spent money on.
(d) Enter the amount spent on each item for each day in their respective columns.
Note: select your own items and the amount spent.
(e) In cells 12 and A8. type “TOTAL N”.
(f) Using formula/function compute the total expenses for each day and for each item.
(g) Create borders around the table.
(h) Insert a footer and type in your full name and index number. (i) Below the table, type in the formula that was used:
(i) in cell 18: (ii) for summing from B3 to H3.
Note: Enclose your formula in quotes ave your work with your full name in the folder created on the desktop.
(k) Print your work and submit to the supervisor.
Using a word Processing application package, create a vising card for a system administrator of a software company using the following specifications:
(a) Size of the card is 3.5″ x 2″, (b) Office and Residential Address separated by a line; (C) the card should be copied m three places on the same page: (d) note that.
(i) the background colour must be grey scale: (ii) the card should be in shadow style, (iii) titlte “Visitor”
Uppercase
Highlight-gray-25%
Font size – 10 pt.
Font type – Georgia:
(iv) Office Address and Residential Address – 1.15 spacing
Font Type-Cambria
Font Size – 7 pt.
(e) Insert a tooter and type in your full name and index number.
(f) Save your work with your full name in the folder created on the desktop.
(g) Print your work and submit to the Supervisor.
(a)(i) Define the term encryption. (ii) Tick two authentication techniques involved in security measure from Table 1.
Table 1
(ii) Outline two features of data encryption. (b) While exchanging data with a friend through your mobile phone, you observed that it took a longer time than usual. Outline four factors that may be responsible for the delay in the data transfer.
|
TECHNIQUE |
TICK() |
|
Firewall |
|
|
Biometric |
|
|
Password |
|
|
Intranet |
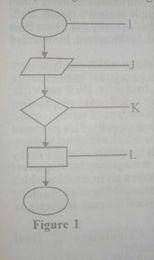
(a) (i) Identify Figure 1 above. (ii) Name the parts labeled I, J, K, and L in Figure 1
(b)(i) Define the documentation stage in the Program Development Life Cycle. (ii) List three characteristics of a good computer program.
(a) Explain the following terms: (i) storage device; (ii) virtual memory.
(b) Two storage devices have capacities 2KB and 2MB respectively. (i) Calculate the number of bits that each of 2KB and 2MB can hold. 2 KB: 2 MB
(i) Putting the two storage together, calculate the total capacity in bytes.
(a) A musician intends to record music on a storage medium. List four ways that the music file can organized in the storage medium.
(b) State two basic operations on computer file. (c) Explain the following computer terms: (i) file (ii) re cord
(a) i() What is firewall? (ii) List two methods used in protecting the computer system.
(b) Explain the following stages of the System Development Life Cycle: (i) feasibility study; (ii) design; (iii) maintenance.
Password reset disk should be created?
- A. every time the user changes password.
- B. once only.
- C. only when the user forgets the password.
- D. twice only
A computer program that gathers information about a person or organization without their knowledge or consent is known as?
- A. Adware.
- B. Time Bomb.
- C. Malware.
- D. Spyware.
Which of the file organization methods can be accessed both randomly and sequentially?
- A. Direct files
- B. Indexed sequential files
- C. Random files
- D. Sequential files
Effects of file insecurity include the following except?
- A. virus infection.
- B. file corruption.
- C. encrypted data
- D. data loss.
The following actions are sources of breaches in computing except?
- A. carelessness
- B. hackers' threat.
- C. piracy.
- D. viruses.
In BCD encoding system, 25, will be represented as?
- A. 01100101
- B. 01010110.
- C. 00100101.
- D. 0101001.
Multiply 101\(_2\) by 11\(_2\)
- A. 1001\(_2\)
- B. 1011\(_2\)
- C. 1110\(_2\)
- D. 1111\(_2\)
A bit as used in computing in digital communication is?
- A. a decimal digit.
- B. an octal digit.
- C. a bin digit.
- D. .a hexadecimal digit.
Which of the options labeled I to IV give two stages involved in booting?
I. Power On self test II. Loading of Operating System IIl. Loading of email IV. Power On Safe Mode
- A. I and Il only
- B. I and III only
- C. Il and IV only
- D. Ill and IV
The disk operating system will label three hard drives as?
- A. A, B and C.
- B. C, D and E.
- C. B, C and D
- D. F, G and H.
After several ‘save’ and ‘delete’ operations, there remain many scattered areas of data too small to be used productively. This describes?
- A. utilization.
- B. protection.
- C. fragmentation.
- D. backing up.
Data that is copied from an application is stored in the?
- A. clipboard.
- B. driver.
- C. prompt.
- D. terminal.
Which of the following is true when data maintained in MS Excel workbook is linked to a word document? The word document
- A. cannot be edited.
- B. must contain a hyperlink.
- C. contains a copy of the actual data.
- D. contains a reference to the original source application.


