(i) The home network of a family has internet access. A server configured to control user access to the network.
State two problems that will likely happen if the children in the family have uncontrolled access to the internet
(ii) The home network of a family has internet access. A server configured to control user access to the network.
Suggest how the problems in 1(a)(i) can be prevented.
1(b) The home network of a family has internet access.
A server configured to control user access to the network.
Give one reason for the user control access
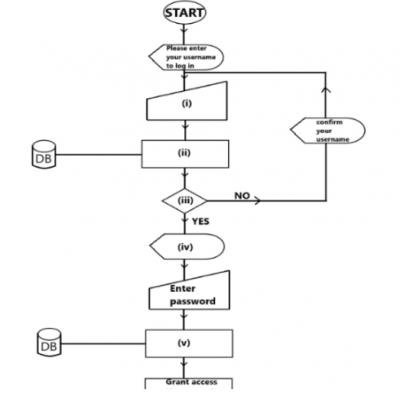
c(i) To have access to the network, each user logs in with a username and password. The flowchart in Figure 1 illustrates the authentication process required to log in. Use the information below to complete the flowchart by placing the letters A to E in the appropriate flowchart symbol numbered (i) to (v) :
A – “Please, enter password to log in”
B – Is the username found?
C – Search the username in the database.
D – Check the password.
E – Enter the username.
(i) ___________________________________________
c(ii) A – “Please, enter password to log in”
B – Is the username found?
C – Search the username in the database.
D – Check the password.
E – Enter the username.
(ii) ___________________________________________
c(iii) A – “Please, enter password to log in”
B – Is the username found?
C – Search the username in the database.
D – Check the password.
E – Enter the username.
(iii)___________________________________________
c(iv) A – “Please, enter password to log in”
B – Is the username found?
C – Search the username in the database.
D – Check the password.
E – Enter the username.
(iv) ___________________________________________
c(v) A – “Please, enter password to log in”
B – Is the username found?
C – Search the username in the database.
D – Check the password.
E – Enter the username.
(v) ___________________________________________
Explanation
a(i) - Exposure to Inappropriate Content
- Addiction and Excessive Screen Time
- Negative Impact on Mental Health
- Phishing and scams (to deceive them into revealing sensitive personal or financial information)
- Cyberbullying and Online Harassment
(ii) - Exposure to Inappropriate Content:
- Use parental control software to filter and block inappropriate websites and content.
- Enable safe search settings on search engines.
- Educate children about the importance of avoiding certain types of content and how to report anything they come across.
Addiction and Excessive Screen Time:
- Set limits on screen time for different activities, such as leisure, homework, and physical activities.
- Encourage a balance between online and offline activities, including hobbies and sports.
- Use apps and features that allow you to manage and monitor screen time.
Negative Impact on Mental Health:
- Foster an open environment where children feel comfortable discussing their emotions.
- Educate them about the potential downsides of comparing themselves to others online.
- Encourage offline activities that promote well-being, such as spending time outdoors, reading, or creative hobbies.
Phishing and scams:
- Teach children about the concept of phishing and scams, explaining how cybercriminals use deception to trick them.
- Make them aware of common phishing tactics, such as fake emails, messages, websites, and offers that seem too good to be true.
- Instruct children to be cautious of unsolicited emails or messages, especially those asking for personal or financial information.
Cyberbullying and Online Harassment:
- Encourage open communication with the children so they feel comfortable discussing any issues they encounter online.
- Teach them about responsible and respectful online behavior.
- Monitor their social media accounts and friends list, ensuring they're not exposed to harmful interactions
(b)- Security and Privacy: User access control ensures that only authorized individuals can access sensitive data, confidential documents, or critical systems. This prevents unauthorized users from compromising the security of the network and helps protect the privacy of personal information.
- Risk Management: User access control reduces the risk of data breaches, insider threats, and cyberattacks. It limits the potential damage that can be caused by unauthorized users who might accidentally or intentionally misuse data or systems.
- Audit Trail and Accountability: Access control systems often provide logs and audit trails, allowing the family to track who accessed what and when. This enhances accountability and aids in investigating any suspicious activities
(c) E - Enter the username.
C - Search the username in the database
B - Is the username found?
A - "Please, enter password to log in"
D - Check the password.

