In changing the storage location of a file, the command to use is_______
- A. ctrl + S keys
- B. 'save' command
- C. 'save as' command
- D. alt + F, then save
Use Table 3 to answer the questions below
| A | B | C | D | E | |
| 1 | BOOK SUPPLIED TO SENIOR HIGH SCHOOLS | ||||
| 2 | MATHS | ICT | ENGLISH | ||
| 3 | SHS1 | 3450 | 4500 | 5678 | |
| 4 | SHS11 | 8765 | 6580 | 9000 | |
| 5 | SHS111 | 2456 | 4009 | 4400 |
Which cells in table 3 contain numeric data with the least value?
- A. A5
- B. B5
- C. C5
- D. D5
Use Table 3 to answer the questions below
| A | B | C | D | E | |
| 1 | BOOK | SUPPLIED | TO SENIOR | HIGH | SCHOOL |
| 2 | MATHS | ICT | ENGLISH | ||
| 3 | SHS1 | 3450 | 4500 | 5678 | |
| 4 | SHS11 | 8765 | 6580 | 9000 | |
| 5 | SHS111 | 2456 | 4009 | 4400 |
The number of cells that contain data in row 1 is_________
- A. 1
- B. 3
- C. 5
- D. 7
Use Table 3 to answer the questions below
| A | B | C | D | E | |
| 1 | BOOK SUPPLIED TO SENIOR HIGH SCHOOLS | ||||
| 2 | MATHS | ICT | ENGLISH | ||
| 3 | SHS1 | 3450 | 4500 | 5678 | |
| 4 | SHS11 | 8765 | 6580 | 9000 | |
| 5 | SHS111 | 2456 | 4009 | 4400 |
In table 3, the content of cell C5________
- A. 2456
- B. 4009
- C. 4400
- D. 3450
Which of the following items is not located on the MS Word menu bar?
- A. Home
- B. Open
- C. View
- D. Mailings

In word processing, the icon in Fig.4 is used for __________
- A. Paging
- B. Line Spacing
- C. Numbering
- D. Bulleting
Which of the following software can be used for graphic production?
- A. DOS Editor
- B. PC Writer
- C. Coreldraw
- D. Acrobat Reader
Which of the following is employed in the transfer of data between computers and a network?
- A. Fiber optics
- B. Male connector
- C. Female Connector
- D. USB Port
A modern and a telephone connection are provided. Other things needed to be able to connect a computer to the internet are _______
- A. ISP account and Utility software
- B. Browser and ISP account
- C. ISP account and Network
- D. Browser and Printer
The application software which allows information available on the internet to be obtained is called _________
- A. Browser
- B. World Wide Web
- C. Spreadsheet
- D. Internet Protocol
The most cost-effective and secure way of transmitting confidential messages among the employees of an organization is the ___________
- A. Electronic notice boards
- B. Teleconferencing
- C. E-mail
- D. Social networks
In ring topology, the computer that is allowed to transmit data possesses the ________
- A. Packet
- B. Data
- C. Access method
- D. Token
The acronym HTTP stands for________
- A. Hyper Text Transfer Protocol
- B. Higher Transfer Text Protocol
- C. Hard Text Transfer Protocol
- D. Higher Text Transfer Protocol
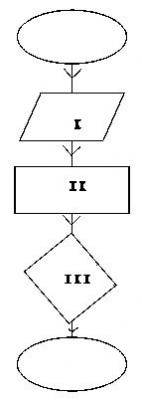
Fig.3 is a flowchart above. Use it to answer the question below
The part labeled III represents________
- A. Process?Action Symbol
- B. Decision Symbol
- C. Read/Write Symbol
- D. Stop Symbol
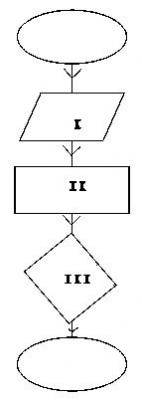
Fig.3 is a flowchart. Use it to answer the question below
The part labelled II represents______
- A. Decision Symbol
- B. Read/Write Symbol
- C. Process Symbol
- D. Stop/End Symbol
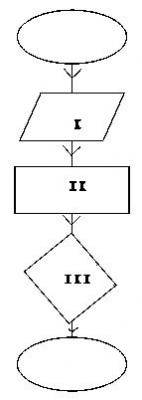
Fig.3 is a flowchart. Use it to answer the question below
The part labelled I represents_________
- A. Begin/Start Symbol
- B. Process/Action Symbol
- C. Read/Write Symbol
- D. Stop/End Symbol
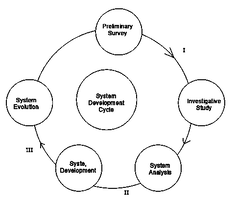
Fig.2 is a system development cycle. Use it to answer the question Above
The path labelled III is the _________?
- A. System design
- B. System implementation
- C. Study review
- D. Feasibility study
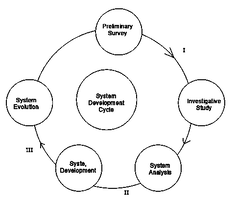
Fig.2 is a system development cycle. Use it to answer the question below
The path labelled II is the __________?
- A. System design
- B. System implementation
- C. Study review
- D. Feasibility study
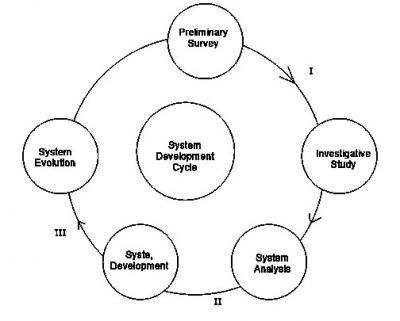
Fig.2 is a system development cycle. Use it to answer the question below
The path labelled I is the __________?
- A. System design
- B. System implementation
- C. Study review
- D. Feasibility study
Which of the following programming languages needs no translator for it to run?
- A. High-Level Language
- B. Low Level Language
- C. Machine Language
- D. Assembly Language
Which of the following methods is not suitable for securing files?
- A. Use of backup
- B. Use of antivirus
- C. Saving documents without a password
- D. Proper labelling of storage devices


