(a) With reference to database management system, state:
one difference between fragmentation and replication.
(a) Name two computer professionals that use CorelDraw in the performance of their duties
(b)(i) List three tools in the CorelDraw toolbox.
(ii) Give one function of each tool listed 3(b)(i)
(c) State two uses of CorelDraw as an application software.
(a)(i) What is malware in computing?
(ii) List three types of malware
(b) State three symptoms of malware infection
(c) Give two ways of preventing malware infection
State one function for each of the following utility program
(a) Disk space analyzer
(b) Backup utility
(c) Register cleaner
(d) File manager
(e) Uninstaller
Which of the following data elements ranks highest in size?
- A. Field
- B. Byte
- C. Record
- D. Bit
The following terms describe the importance of data security except data
- A. availability
- B. integrity
- C. normalization
- D. consistency
The allocation and de-allocation of computing resources in a computer is the function of
- A. browsers
- B. operating system
- C. application software
- D. memory unit
Use the information below to answer questions 13 and 14.
A student in the school hostel was able to upload some personal details on the school portal via the school’s WiFi .
The ISP and the hostel are both domiciled in the school premises.
The physical infrastructure through which internet traffic are exchanged between the ISP in the school illustrated above and other ISP s is called
- A. switch racks
- B. subscriber end points
- C. internet exchange point
- D. server farms
Use the information below to answer questions 13 and 14.
A student in the school hostel was able to upload some personal details on the school portal via the school’s WiFi .
The ISP and the hostel are both domiciled in the school premises.
What type of network is illustrated above?
- A. MAN
- B. WAN
- C. LAN
- D. PAN

The equipment shown in Figure 1 is used for
- A. infrared transmission
- B. ethernet connection
- C. audio transmission
- D. radio transmission
A computer system under use was found to be unusually slow, freezes often and very dusty. What is needed to correct this problem?
- A. Hit the system unit with a blower
- B. Delete some files
- C. Change the location of the computer
- D. Perform maintenance procedure
The process of drawing inference from a piece of information is called
- A. interpretation
- B. analysis
- C. collation
- D. organization
Computer ethical practises include the following except
- A. respect for intellectual property
- B. exposure of vulnerability in websites
- C. use of polite words on other users
- D. use of other people’s computer without due permission
Use Table 1 to answer questions 35 and 36.
Table 1: TableStudent
| Reg No | House |
Age |
| 18/001 | Yellow | 14 |
| 18/002 | Blue | 15 |
| 18/003 | Yellow | 15 |
The attributes in Table 1 are
- A. Yellow, Blue, Yellow
- B. 14, 15, 15
- C. Reg. No, House, Age
- D. 18/001, 18/002, 18/003
Use Table 1 to answer questions 35 and 36.
Table 1: TableStudent
| Reg No | House |
Age |
| 18/001 | Yellow | 14 |
| 18/002 | Blue | 15 |
| 18/003 | Yellow | 15 |
Columns 2 and 3 in Table 1 cannot be used as primary key because both fields contain
- A. different datatypes
- B. duplicate values
- C. the same datatype
- D. only strings and numbers respectively
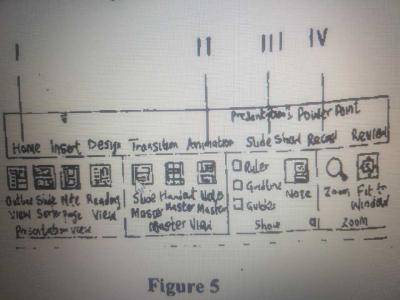
Figure 5 is an MS PowerPoint application interface. The part used to apply motion effect to different objects of a slide is labelled
- A. III
- B. I
- C. II
- D. IV
People who use cathode ray tube monitor without antiglare screen are susceptible to
- A. blurred vision
- B. back ache
- C. repetitive strain injury
- D. stiffness of the wrist
Macromedia Dreamweaver application is used for
- A. surfing the internet
- B. graphic design
- C. intranet communication
- D. web design
Artificial intelligence is a feature of
- A. fifth generation computers
- B. third generation computers
- C. second generation computers
- D. fourth generation computers
The following precautionary measures are taken against virus infection except
- A. downloading e-mail and attachment before scanning it
- B. avoiding booting the computer with disks in it
- C. regular updating of antivirus.
- D. avoiding the installation of piratted software
A digital platform for the delivery of public sector information and seminar to citizens is called
- A. e-library
- B. e-commerce
- C. e-learning
- D. e-government


