A student was asked to record the type of vehicle that entered the school compound through the school’s main gate on a Monday morning. The passage below is an excerpt from the student’s report on the assignment. “Report on the vehicular traffics at the gate on Monday.
1. Introduction; I was directed by the school principal to sit at the main gate and record the type and number of vehicles that passed through the gate on Monday morning.
2. Observation; I arrived at the gate at about 8;00am and left at 12 noon. During this period, I made the following observation; Car, bus, bus, car, lorry, motorcycle, car, tricycle, motorcycle, bus, bus.”
(a) Beginning from the desktop, outline a step by step procedure of how to type the passage in MS word, using A4 paper size and portrait orientation.
(b) State the procedure for carrying out the following operations in the passage;
(i) Begin the second and third sentences in new paragraphs; (ii) Write the first sentence in capital letter underline it and bold it. (iii) Begin the first letter of a sentence with capital letters (iv) Represent the student’s observation in a table with three columns under the headings; Serial Number, Type of vehicle, Number of vehicle (v) Merge the first two cells of the ast row of the table and type “Total”and give the total number of vehicles observed in the column for number of vehicles (vi) Save the document with the name: “Vehicular traffic”(vii) Print the document.
Given an internet connected computer, outline a step by step procedure for carrying out the following operations;
(a) How to log on to www.mybooks.com and obtain the prices of books W, X, Y, Z and M.
(b) How to tabulate the prices in a worksheet, showing the prices in dollars and the naira equivalent, for each book and save the workbook as “Prices of Books”. Assume that the prices of the books are given in dollars, [use $1.00=N120.00].
(c) How to send the workbook in 5(b) as an attachment to your father’s email address ([email protected]) with the subject “Price of Books”.
(a) Define;
(i) Data Security (i) Data risk assessment
(b)(i) What is Access Control
(ii) List the access control methods in database security.
(c) State three roles of a database administrator.
(a)(i) Define application package.
(ii) State one use each of any four application packages
(b) List two benefits of a presently package
(c) Outlines three guidelines for creating a good MS PowerPoint Presentation
(a) Define the following
(i) Database
(ii) Database management system
(b) Mention three functions of a database management system.
(c) Mention two ways through which data can be destroyed.
(d) State three precautionary measure to prevent data loss.
a (i) Define an operating system.
(ii) State two functions of an operating system
(iii) List two differences between an operating system and application system software.
b Starting from the Save As dialogue box, outline the steps involved in passwording a document in a word processing package.
The exchange of information over a network follows a set of rules called
- A. transmission rules
- B. transfer rules
- C. channels rules
- D. protocols
In a relational database management system, files are organized as relations and
- A. tuple
- B. modules
- C. tables
- D. forms
One of the advantages of a parallel database is
- A. data sharing
- B. data security
- C. faster processing of data
- D. uniform memory access
A program developed to protect the computer from malicious software is referred to as
- A. trojan
- B. driver
- C. antivirus
- D. spyware
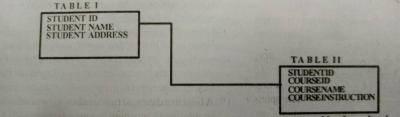
The diagram illustrates the relationship between two tables in a database.
What type of relationship exists between Tables I and II?
- A. one to one
- B. three to four
- C. four to three
- D. one to many
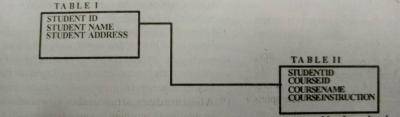
The diagram illustrates the relationship between two tables in a database.
The student ID in Tables II is referred to as
- A. primary key
- B. foriegn key
- C. normal key
- D. composite key
Which of these measures would not secure data in database?
- A. Encryption
- B. Data integration
- C. Personal Identification Number
- D. Username and passwords
The type of file organisation in a DVD-ROM is?
- A. direct access
- B. sequential
- C. serial
- D. hierarchical
The following are desturctive software except
- A. drivers
- B. worms
- C. trojan horses
- D. logic bomb
Which of the following is not a computer professional?
- A. Network Administrator
- B. Web Master
- C. System Analyst
- D. File Manager
Which of the following is not a safety equipment in a computer laboratory?
- A. surge protector
- B. metal detector
- C. smoke detector
- D. fore extinguisher
Which of the following is not a preventive maintenance measure?
- A. Regular update of the operating system
- B. Proper shut down of the system
- C. use of uninterrupted power supply
- D. data recovery
A file kept in case of an accident or natural disaster is called
- A. master
- B. transition
- C. back-up
- D. reference
In MS Powerpoint, the action of holding down the left mouse key and moving the mouse around the slide would
- A. highlight an item
- B. drag an item
- C. select an item
- D. move an item
The study of the effect of interaction between the computer and human users is referred to as computer
- A. ergonomy
- B. economy
- C. ergophobia
- D. biomechanics


