A computer program that gathers information about a person or organization without their knowledge or consent is known as?
- A. Adware.
- B. Time Bomb.
- C. Malware.
- D. Spyware.
Which of the file organization methods can be accessed both randomly and sequentially?
- A. Direct files
- B. Indexed sequential files
- C. Random files
- D. Sequential files
Effects of file insecurity include the following except?
- A. virus infection.
- B. file corruption.
- C. encrypted data
- D. data loss.
The following actions are sources of breaches in computing except?
- A. carelessness
- B. hackers' threat.
- C. piracy.
- D. viruses.
In BCD encoding system, 25, will be represented as?
- A. 01100101
- B. 01010110.
- C. 00100101.
- D. 0101001.
Multiply 101\(_2\) by 11\(_2\)
- A. 1001\(_2\)
- B. 1011\(_2\)
- C. 1110\(_2\)
- D. 1111\(_2\)
A bit as used in computing in digital communication is?
- A. a decimal digit.
- B. an octal digit.
- C. a bin digit.
- D. .a hexadecimal digit.
Which of the options labeled I to IV give two stages involved in booting?
I. Power On self test II. Loading of Operating System IIl. Loading of email IV. Power On Safe Mode
- A. I and Il only
- B. I and III only
- C. Il and IV only
- D. Ill and IV
The disk operating system will label three hard drives as?
- A. A, B and C.
- B. C, D and E.
- C. B, C and D
- D. F, G and H.
After several ‘save’ and ‘delete’ operations, there remain many scattered areas of data too small to be used productively. This describes?
- A. utilization.
- B. protection.
- C. fragmentation.
- D. backing up.
Data that is copied from an application is stored in the?
- A. clipboard.
- B. driver.
- C. prompt.
- D. terminal.
Which of the following is true when data maintained in MS Excel workbook is linked to a word document? The word document
- A. cannot be edited.
- B. must contain a hyperlink.
- C. contains a copy of the actual data.
- D. contains a reference to the original source application.
Spreadsheet packages can be used for? .
- A. database and painting.
- B. drawing and painting.
- C. budgeting and inventory.
- D. word processing and drawing
A cell with a red triangle in the top-right comer in a spreadsheet application signifies?
- A. an error in the cell.
- B. a comment associated with the cell.
- C. that the font colour for the text in the cell is red.
- D. that a formula cannot be entered into the cell.
In Microsoft PowerPoint, two kinds of sound effect files that can be added to a presentation are?
- A. .wav files and .mid files.
- B. .wav files and .gif files.
- C. .wav files and jpg files.
- D. jpg files and.gif files.
To hold row and column titles in places so that they do not scroll when the user scrolls a worksheet, click the?
- A. freeze panes command on the windows menu.
- B. hold titles command on the edit menu.
- C. split command on the windows menu.
- D. show grid command on the windows menu.
One major difference between paper spreadsheet and electronic spreadsheet is?
- A. a management of columns.
- B. headings from formatting.
- C. arrangement of rows. .
- D. speed of processing
In MS Excel, the cell that contains the pointer or cursor is called?
- A. active cell.
- B. current cell.
- C. default cell.
- D. passive cell.
The major advantage of free software is that it is?
- A. free and contains unlimited components.
- B. licensed and available always.
- C. licensed and can be copied by anyone.
- D. superior in quality but not robust.
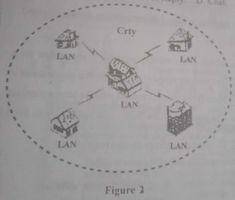
What type of network is represented in Figure 2?
- A. Local Area Network
- B. Metropolitan Area Network
- C. Personal Area Network
- D. Wide Area Network
To send a created MS PowerPoint document using email to a user, the document can be added as?
- A. Attachment.
- B. Draft.
- C. Reply.
- D. Chat.


